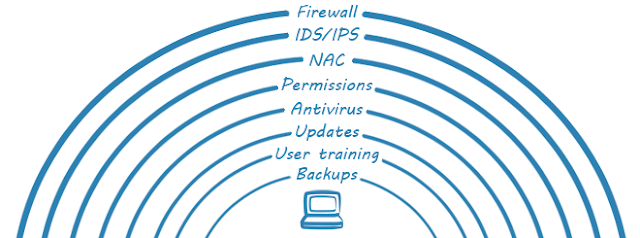
Defense in depth is an information assurance (IA) concept in which multiple layers of security controls (defense) are placed throughout an information technology (IT) system.
The idea behind the defense in depth approach is to defend a system against any particular attack using several independent methods. It is a layering tactic, conceived by the National Security Agency (NSA) as a comprehensive approach to information and electronic security. Defense in depth is originally a military strategy that seeks to delay rather than prevent the advance of an attacker by yielding space to buy time.
Defense in depth can be divided into three areas of controls:
Physical controlsPhysical controls are anything that physically prevents access to IT systems. For Example Guards, dogs, CCTV systems, etc.
Technical controls
Technical controls are hardware or software whose purpose is to protect systems and resources. Examples of technical controls would be disk encryption, fingerprint readers, and Windows Active Directory. Hardware technical controls differ from physical controls in that they prevent access to the contents of a system, but not the physical systems themselves.
Administrative controls
Administrative controls are an organization's policies and procedures. Their purpose is to ensure that there is proper guidance available in regards to security and that regulations are met. They include things such as hiring practices, data handling procedures, and security requirements.
What layers to protect:
1- Data.2- OS.
3- Applications.
4- Infrastructure.
5- Management.
6- People.
7- Physical assets.
What solutions to use to constitutes the defense in depth:
> Antivirus software
> Authentication and password security
> Biometrics
> Demilitarized zones (DMZ)
> Data-centric security
> Encryption
> Firewalls (hardware or software)
> Hashing passwords
> Intrusion detection systems (IDS)
> Logging and auditing
> Multi-factor authentication
> Vulnerability scanners
> Physical security (e.g. deadbolt locks)
> Timed access control
> Internet Security Awareness Training
> Virtual private network (VPN)
> SandboxingIntrusion Protection System (IPS)
How it constitutes the defense in depth layers:
Because there are so many potential attackers with such a wide variety of attack methods available, there is no single method for successfully protecting a network. Using the strategy of defense in depth will reduce the risk of having a successful attack on a network.For Example in case a script kiddie trying to hack a system using knowing tools, firewalls will be effective because firewall manages both incoming and outgoing traffic on a network with allowing and deny options, but relying on firewall only is a big mistake.
Network-based intrusion detection systems (IDS) provide another layer of defense. A network-based IDS will monitor network traffic to identify scans or traffic patterns that indicate an attack. These systems can recognize defined attack signatures or anomalous behavior that might be indicative of an attack.
However, support the hacker is a skilled attacker that will study and monitor the target then use advanced techniques including social engineering attacks. in this case, the first layer of defense is to raise the awareness, then implement physical security, set complex passwords for systems, use a one-time password, and ensure to have an anti-virus.
The worst case is when the attacker is a trusted employee, in addition to the above layers of defense Policies and procedures, employee screen monitor, accountability, and authorization are important methods to secure the network from attackers who already have trusted access to it.



0 Comments