Microsoft office implements safe links which are originally designed to protect users from malware and phishing attacks
safe links has been implemented by Microsoft in office 365 as part of its ATP (Advanced Threat Protection ) solution that works by replacing all URLs in an incoming email with Microsoft secure URLs
so every time users click on any link in an email safe links will send the link to Microsoft owned domain to check and verify if the link is safe , if it finds out that the link is malicious it alerts the user .
Supported by all modern web browsers, zero-width space (ZWSP) is a non-printing character used in computerized typesetting to indicate word boundaries to text processing systems when using scripts that do not use explicit spacing, or after characters (such as the slash) that are not followed by a visible space but after which there may nevertheless be a line break.
Normally, it is not a visible separation, but it may expand in passages that are fully justified.
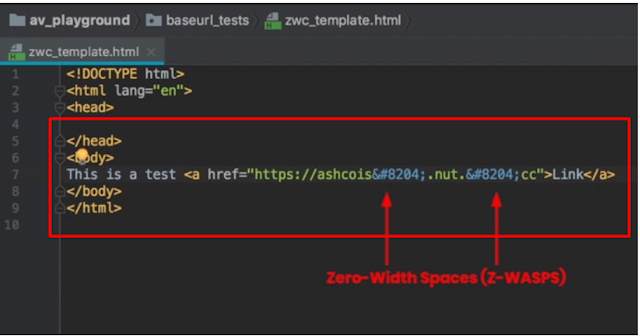
How Zero-Width Space Phishing Attack work ?
Attackers are simply adding multiple zero-width spaces within the malicious URL in their phishing emails, breaking the URL pattern in a way that Microsoft does not recognize it as a link. Researchers also provided a video demonstration showing what happened when they sent a malicious URL to an Office 365 with Zero-Width Space and without it .




0 Comments