recent
Recent posts
Cystack Threat Hunting Team Report - Stealthy Owl
The threat hunting and incident response team at Cystack has discovered and analyzed a malicious attack that might affec…
Is trust working against you?
"Trust is highly specific. You can trust me to help you select a single malt Scotch whiskey, but you should defin…
All you want to know about Google Hacking
Google hacking , also named Google dorking , is a computer hacking technique that uses Google Search and other Googl…
Operating Systems Detection using Ping
Ping is a computer network administration software utility, which operates by sending Internet Control Message Protoco…
File Compression
Each day we deal with tons of files and pictures and we come across different formats some of them are compressed, whi…
Zero-Day in Windows 10 allows files to be overwritten !
A security researcher has released proof-of-concept code for a zero-day exploit in Windows10 The bug was revealed by …
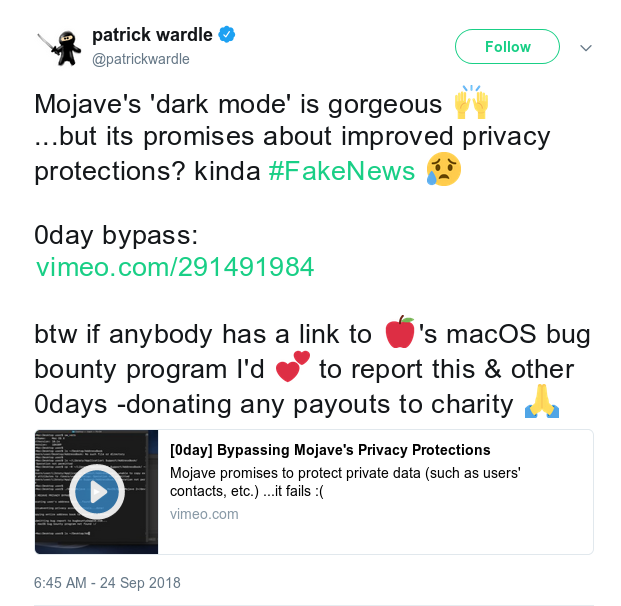
0-day vulnerability affects all versions of MacOs
Last week Apple announced its latest release of MacOs ; the “ Mojave ” release, at the same date a security researche…
Popular Posts

USB Killer Burns Firewall in less than a Second!